While most crypto exchanges verify users through automated document checks (95%+ of cases), some platforms conduct live KYC verification calls for high-risk accounts or when automated systems flag issues. These calls add a human review layer during Enhanced Due Diligence (EDD), affecting less than 5% of users. With rising fraud and data breaches, understanding this process is key to staying secure and compliant in the crypto space. Below is a complete guide, from how these calls work to best practices for both exchanges and traders.
Key Takeaways
- KYC verification calls add a human layer to identity checks beyond document uploads.
- They strengthen Anti-Money Laundering (AML) compliance by adding human verification for high-risk cases such as Politically Exposed Persons (PEPs), users from sanctioned countries, or accounts with suspicious transaction patterns. This aligns with Financial Action Task Force (FATF) Recommendation 15, which requires Enhanced Due Diligence (EDD) for such accounts. – the global standard-setting body for combating money laundering and terrorist financing, whose guidelines influence regulations in 200+ jurisdictions.
- Emerging technologies like Self-Sovereign Identity (SSI) and Zero-Knowledge Proofs (ZKP) show promise for future privacy-preserving verification, but remain in pilot phase as of 2025 with no regulatory approval for crypto KYC. Today, exchanges and users must follow centralized KYC protocols with encrypted storage and access controls to ensure data safety.
What Is a Crypto KYC Verification Call?
A crypto KYC verification call is a live voice or video session conducted by an exchange or compliance provider to verify a user’s identity. Unlike electronic KYC (eKYC) that relies solely on document uploads, these calls include real-time interaction to confirm information. Live verification calls are NOT part of standard crypto onboarding. Major exchanges like Binance, Bybit, Coinbase, and Kraken verify 95%+ of users through automated eKYC—uploading ID, taking a selfie, and receiving approval within 5-20 minutes—without any human interaction.

Calls are reserved for Enhanced Due Diligence (EDD) situations:
1. Automated Verification Fails:
- Document quality issues (blurry photo, damaged ID, expired)
- Liveness detection failure (selfie doesn’t match ID, suspected deepfake)
- Address verification incomplete (proof of address outdated, name mismatch)
2. High-Risk Indicators Trigger Manual Review:
- Politically Exposed Person (PEP): Government official, judge, military officer, or immediate family member
- High-risk jurisdiction: User from FATF blacklist/graylist countries or sanctioned regions
- Large transaction volumes: Deposits exceeding $10,000/day or withdrawals above $50,000/month (thresholds vary by exchange)
- Suspicious patterns: Rapid deposit-withdrawal cycles, connections to mixing services, flagged wallet addresses
3. Regulatory Requirement:
- Government request for additional verification during audit
- Exchange internal risk assessment flags account for manual review
- Cross-platform suspicious activity reports (SARs)
Why Exchanges Avoid Calls When Possible:
- Cost: $15-30 per call vs $0.50-2 for automated eKYC
- Scalability: Compliance officers can handle 10-20 calls/day vs automation processing millions
- User friction: Scheduling hassles, timezone mismatches reduce conversion rates
- Speed: Calls take 1-3 days (scheduling + review) vs 5-20 minutes for automation
Purpose of KYC Verification Calls:
1. Regulatory Compliance:
- US: Meet Bank Secrecy Act (BSA) requirements enforced by FinCEN. Crypto exchanges classified as Money Services Businesses (MSBs) must implement AML programs, conduct Customer Due Diligence (CDD), and submit Suspicious Activity Reports (SARs) for transactions ≥$5,000 suspicious activity.
- EU: Comply with Markets in Crypto-Assets (MiCA) framework (effective Dec 2024) and AMLD5/6 (5th & 6th Anti-Money Laundering Directives), which mandate risk-based KYC for Virtual Asset Service Providers (VASPs).
- Global: Align with FATF Recommendation 15, extending full AML/CFT obligations to crypto sector. Travel Rule requires sharing sender/recipient info for transactions ≥$3,000 (US) or ≥€1,000 (EU).
2. Fraud Prevention:
- Detect synthetic identities (fake IDs created from real stolen data + fabricated info).
- Prevent account takeovers (attacker with stolen documents cannot pass live video call).
- Block terrorist financing and sanctions evasion (OFAC list screening).
3. Enhanced Due Diligence (EDD):
- CDD is baseline verification (ID + address + basic risk screening) for all users.
- EDD is deeper investigation for high-risk accounts: PEPs, large transactions, suspicious patterns.
- Calls allow compliance officers to ask source-of-funds questions, assess user credibility in real-time.

4. KYC Calls vs. Document-Only eKYC:
| Feature | Automated eKYC (Standard) | Manual Document Review | EDD with Verification Call |
|---|---|---|---|
| Used For | 95%+ of users | Failed auto-verification (unclear docs) | High-risk accounts (PEP, large volumes, suspicious flags) |
| Process | Upload ID → Selfie → AI verification | Human reviews documents, no call | Manual review + scheduled video/voice call |
| Time to Approval | 5-20 minutes | 1-2 business days | 1-3 business days (depends on scheduling) |
| Liveness Detection | Advanced (3D face mapping, blink detection, head movement) | N/A (static document review) | Real-time video interaction (highest confidence) |
| Fraud Detection Rate | 85-90% | 90-95% | 95-98% |
| Cost to Exchange | $0.50 – $2.00 per verification | $5 – $15 per review | $15 – $30 per call |
| Scalability | Unlimited (millions/day) | Moderate (hundreds/day) | Very Limited (10-20 calls/officer/day) |
| User Experience | Seamless, instant feedback | Wait for human review | Scheduling hassle, timezone coordination |
| Regulatory Compliance | Meets CDD requirements (FATF, FinCEN) | Enhanced document scrutiny | Full EDD per AML regulations |
| Example Platforms | Bybit Level 1, Binance Verify, Coinbase Basic | Most major exchanges for edge cases | Rare; used by traditional banks, regulated brokers entering crypto |
Note: These methods are NOT mutually exclusive. All exchanges use automated eKYC as the default. Manual review is triggered when automation cannot confidently verify documents. Calls are the final escalation for accounts requiring Enhanced Due Diligence per regulatory requirements.
The Role of KYC Verification Calls in Crypto Compliance
How Verification Calls Fit Into Crypto Compliance
Crypto exchanges follow a tiered KYC framework mandated by FATF and national regulators:
Tier 1 – Basic CDD (Customer Due Diligence):
- Applies to: All users, regardless of transaction size
- Process: Automated eKYC (ID upload + selfie + address verification)
- Verification: AI-based document authentication + biometric face match
- Time: 5-20 minutes
- Example: Bybit Level 1 (withdrawals up to $1M/day), Coinbase Basic
Tier 2 – Enhanced Document Verification:
- Applies to: Users with unclear documents OR medium transaction volumes ($10,000-50,000/month)
- Process: Human compliance officer reviews documents manually, no call
- Verification: Checks for photo tampering, expired IDs, address consistency
- Time: 1-2 business days
- Example: Bybit Level 2 (withdrawals up to $2M/day)
Tier 3 – Enhanced Due Diligence (EDD) with Calls:
- Applies to: High-risk accounts per AML regulations
- Politically Exposed Persons (PEPs)
- Users from FATF high-risk jurisdictions
- Transaction volumes exceeding thresholds (>$50,000/month varies by exchange)
- Suspicious activity flags (mixing services, sanctioned wallets)
- Process: Manual review + scheduled verification call (video/voice)
- Verification: Compliance officer interviews user, confirms source of funds, assesses responses for fraud indicators
- Time: 1-3 business days (scheduling dependent)
- Example: Required for institutional accounts (hedge funds, OTC desks), high-net-worth individuals
Why Tiered Approach?
- Risk-based: FATF Recommendation 1 requires risk-proportionate measures (don’t apply EDD to all users → wastes resources)
- User experience: Low-risk users get fast approval; high-risk users get thorough scrutiny
- Cost efficiency: Automated eKYC handles 95% of volume; expensive calls reserved for 5% that need it
Compliance Pressure:
| Region | Regulatory Body | KYC Requirements | Penalties for Non-Compliance | Notes |
|---|---|---|---|---|
| United States | FinCEN (AML enforcement), SEC (securities), CFTC (commodities) | • MSB registration with FinCEN • Implement AML program (BSA) • Collect: Name, DOB, address, SSN • Verify: Government-issued ID • File SARs for suspicious activity ≥$5,000 • Travel Rule: Share sender/recipient info for transactions ≥$3,000 |
• FinCEN fined 17 crypto platforms $210M total in 2023 • Bittrex: $53M settlement (2022) • Criminal charges possible for willful violations |
State licenses also required (e.g., NY BitLicense) |
| European Union | EBA (European Banking Authority), National FIUs (Financial Intelligence Units) | • MiCA compliance (effective Dec 2024) • AMLD5/6 implementation • Collect: Full name, DOB, address, nationality, tax ID • Verify: Government-issued ID, proof of address • PEP screening • Travel Rule: ≥€1,000 transactions |
• Revolut: €3.5M fine (Lithuania, April 2025) for AML shortcomings • Barclays: £42M fine (UK FCA, July 2025) for inadequate KYC |
MiCA creates unified framework (previously fragmented by country) |
| United Kingdom | FCA (Financial Conduct Authority) | • FCA registration for crypto firms • Risk-based CDD • Collect: Name, DOB, address • Verify: ID + proof of address within 3 months • Enhanced verification for PEPs • Ongoing monitoring |
• Heavy fines for unregistered operations • FCA rejected 75%+ of crypto firm applications (2021-2023) |
Post-Brexit, UK follows own rules (not MiCA) but aligned with FATF |
| APAC – Singapore | MAS (Monetary Authority of Singapore) | • Payment Services Act license • Full KYC before account opening • Collect: ID, address, employment, source of funds • EDD for transactions >S$20,000 |
• License revocation • Criminal penalties for unlicensed operations |
One of strictest regimes in Asia |
| APAC – South Korea | FSC (Financial Services Commission), KoFIU | • Real-name verification system (2018) • Crypto accounts linked to identically-named bank accounts • ISMS cybersecurity certification • Virtual Asset User Protection Act (2023) |
• Market consolidation: Most small exchanges shut down due to high compliance costs | Banned anonymous trading entirely |
| APAC – Japan | FSA (Financial Services Agency) | • Crypto exchange registration • Standard KYC: ID + address + selfie • Ongoing monitoring • Customer asset segregation |
• Coincheck hack (2018): Lost license temporarily, implemented enhanced security | Progressive regulatory environment, supports innovation with oversight |
| Canada | FINTRAC, CSA/IIROC (provincial securities) | • MSB registration with FINTRAC (since 2014) • Provincial securities registration • Full KYC + AML compliance • Crypto treated as property (capital gains tax) |
• Fines for unregistered operations • Strong enforcement since 2014 (driven by terrorism financing concerns) |
Clear regulatory framework, high compliance rates |
Key Abbreviations:
- AML: Anti-Money Laundering
- CDD: Customer Due Diligence (baseline KYC)
- EDD: Enhanced Due Diligence (for high-risk)
- PEP: Politically Exposed Person
- SAR: Suspicious Activity Report
- FATF: Financial Action Task Force (global standards)
- Travel Rule: Requirement to share sender/recipient info for large transactions
Step-by-Step Crypto KYC Verification Call Process
Step 1: Pre-Call Preparation (24-48 hours before scheduled call)
What Happens:
- User receives email/SMS notification: “Your account requires Enhanced Due Diligence verification. Please schedule a verification call within 7 days to avoid account restrictions.”
- Email includes:
- Link to online booking system (calendar with available time slots)
- Checklist of required documents
- Technical requirements (stable internet, camera, microphone)
- Timezone conversions (if user in different region than compliance team)
Documents to Prepare:
1. Government-Issued Photo ID (Primary Identity Document):
- Accepted: Passport, national ID card, driver’s license
- Requirements:
- Must be valid (not expired—check expiration date!)
- All four corners visible in photo/scan
- No glare or shadows obscuring text
- Color photo (not black & white)
- Issued by recognized government authority
- Not Accepted: Student IDs, employee badges, expired documents, photocopies

2. Proof of Address (dated within 3 months):
- Accepted:
- Utility bill (electricity, water, gas, internet)
- Bank statement (showing name + address)
- Rental agreement or lease (signed by landlord)
- Government-issued document with address (tax statement, voter registration)
- Requirements:
- Name on document must match ID exactly
- Full address visible (street, city, postal code)
- Issued within last 90 days (some exchanges accept 6 months)
- Original document, not screenshot or altered version
- Not Accepted: Mobile phone bills (varies by exchange), credit card statements (privacy concerns), hotel receipts
3. Source of Funds Documentation (if requested by compliance team):
- For employees: Pay stubs (last 2-3 months), employment contract
- For business owners: Business registration, tax returns, articles of incorporation
- For investors: Brokerage statements, sale of property documents, inheritance papers
- For crypto traders: Transaction history from other exchanges, tax filings showing crypto income
4. Blockchain Wallet Address (if exchange requires):
- Why needed: Compliance teams verify your withdrawal address isn’t linked to sanctioned wallets (OFAC list), mixing services, or known scam addresses
- How to provide: Copy your wallet address from MetaMask/Ledger/Trust Wallet, paste into exchange form
- What they check: Exchange runs blockchain analysis (Chainalysis, Elliptic) to see transaction history, flag risky connections
Technical Setup Checklist:
1. Internet & Devices:
- Stable internet connection (minimum 5 Mbps upload speed—test at speedtest.net)
- Computer or smartphone with working camera (test in selfie mode)
- Working microphone (test with voice recorder app)
- Quiet, well-lit room (no backlighting—sit facing window or lamp)
- Download required video call platform (Zoom, Skype, or exchange’s custom platform)
- Test platform 24 hours before call (some require browser permissions for camera/mic)
2. Avoid These Common Mistakes:
- Using VPN during call (raises red flags—compliance team sees IP mismatch)
- Taking call in car/public place (background noise, poor lighting, privacy concerns)
- Having someone else present unless pre-approved (appears suspicious)
- Name mismatch (ID says “Robert Smith,” proof of address says “Bob Smith”—use legal full name)
- Expired documents (check expiration dates 48 hours before, not morning of call)
3. Scheduling the Call:
- Use exchange’s online booking system (calendar link in email)
- Choose time when you’re alert (not early morning if you’re groggy)
- Consider timezone: If compliance team in US and you’re in Asia, book evening slot (their morning)
- Add 30-min buffer (in case previous call runs over)
- Mark calendar, set phone reminder 1 hour before
4. If You Miss the Scheduled Call:
- Most exchanges allow 1 free reschedule
- After 2+ no-shows: Account may be restricted (view-only mode)
- Some exchanges charge rescheduling fee ($10-25) after first miss
Step 2: Identity Confirmation (First 5-10 minutes of call)
Call Begins:
- Compliance officer introduces themselves: “Hello, this is [Name] from [Exchange] compliance team. I’m conducting your Enhanced Due Diligence verification. This call will be recorded for regulatory purposes. Do you consent to recording?”
- User must explicitly consent: “Yes, I consent.” (If no consent, call cannot proceed per GDPR/privacy laws)
Visual Verification:
Step 2a: Document Presentation
- Officer: “Please hold your [passport/ID] up to the camera so all four corners are visible. Ensure good lighting on the document.”
- User shows physical ID to camera (not scan, not photo of ID)
- Officer checks for signs of tampering:
- Holograms, watermarks, security features
- Font consistency (fake IDs often have mismatched fonts)
- Photo quality (professional photo vs printed photo glued on)
- Expiration date (is it still valid?)

Step 2b: Live Liveness Detection
- Officer: “Now, please look directly at the camera. I’ll ask you to perform a few actions to confirm you’re a real person, not a pre-recorded video or deepfake.”
- Prompts user may receive:
- “Turn your head slowly to the left… now to the right.”
- “Smile.”
- “Blink twice.”
- “Raise your hand and wave.”
- “Say your full name and date of birth.”
- What officer watches for:
- Natural movements (stiff movements = potential deepfake)
- Shadows move correctly (lighting consistency)
- Voice matches lip movements (audio-video sync)
- Real-time response to unexpected prompts (can’t be pre-recorded)
Step 2c: Biometric Comparison
- Officer uses split-screen display: Live video on left, ID photo on right
- Compares:
- Facial structure (cheekbones, jaw line, nose shape)
- Eye color, hair color (accounting for aging, hairstyle changes)
- Distinctive features (moles, scars, tattoos visible in ID photo)
- Some platforms use AI-assisted face matching:
- Software calculates similarity score (e.g., 97% match)
- Officer makes final judgment call (AI assists, doesn’t decide)
Step 2d: Background Checks (Simultaneous with video call)
- While talking to user, compliance officer (or separate team member) runs:
- OFAC sanctions screening: Is user on any prohibited lists? (SDN list, EU sanctions, UN sanctions)
- PEP database search: Is user a Politically Exposed Person? (government official, judge, military officer)
- Adverse media check: Any news articles linking user to fraud, money laundering, terrorism?
- Wallet address analysis: If provided, run through Chainalysis/Elliptic to check for:
- Connections to sanctioned wallets (e.g., North Korea-linked addresses)
- Mixing service usage (Tornado Cash, Blender.io)
- Ransomware payments, darknet market transactions
- If red flags appear: Officer makes note, may ask additional questions later in call (doesn’t confront user immediately unless severe risk)
How Long This Takes:
- Simple case (low-risk user, clear ID): 5 minutes
- Complex case (aged ID photo, need multiple liveness checks): 10-15 minutes
If Identity Cannot Be Verified:
- Officer: “I’m unable to confidently verify your identity at this time. You’ll need to resubmit clearer documents and reschedule. Our team will send an email with specific requirements.”
- Common reasons for failure:
- ID photo too old (15+ years, person’s appearance changed dramatically)
- Poor video quality (pixelated, laggy connection)
- User nervous behavior (excessive sweating, avoiding eye contact—can be cultural, but raises flags)
- Suspected identity theft (someone using stolen documents)
Step 3: Compliance Interview (10-20 minutes)

What Compliance Officers Are Assessing:
- Consistency: Do answers match submitted documents? (e.g., says “I’m a teacher” but no employment docs)
- Credibility: Are responses specific and confident, or vague and evasive?
- Risk factors: Any indications of money laundering, sanctions evasion, or straw man account (acting on behalf of hidden beneficial owner)?
Question Category 1: Source of Funds
Purpose: Verify money entering platform is from legitimate sources, not proceeds of crime
Officer: “What is the primary source of funds you’ll be using on this platform?”
Good Answers (Specific, Verifiable):
- “I’m a software engineer at [Company]. My salary is $X per year. I’ve attached my last two pay stubs.”
- “I own a small business-a coffee shop. I’ve provided business registration and tax returns showing $X annual revenue.”
- “I recently sold a property and received $X. Here’s the sale agreement and bank transfer confirmation.”
- “I received an inheritance of $X from my grandmother’s estate. I have the will and executor documents.”
- “I’ve been trading crypto since 2020 on [Other Exchange]. Here’s my transaction history and tax filings showing $X in capital gains.”
Bad Answers (Vague, Red Flags):
- “I’m a trader.” ← Too vague (trader of what? for whom? how much income?)
- “I have savings.” ← How did you accumulate savings? From what income?
- “A friend sent me money.” ← Who? Why? How much? (Possible money laundering)
- “I prefer not to say.” ← Cannot proceed with EDD without source of funds disclosure
- “I do business.” ← What kind of business? Is it registered? Any documentation?
Question Category 2: Transaction Volume & Patterns
Purpose: Assess whether account activity will match declared source of funds (e.g., don’t claim “$50k salary” then deposit $500k/month)
Officer: “What is your expected monthly transaction volume on our platform? Deposits and withdrawals.”
Good Answers:
- “I plan to deposit around $5,000-10,000 per month from my salary for long-term investment in Bitcoin and Ethereum. I don’t plan to day trade.”
- “My business generates $50,000/month revenue. I’ll convert 10-20% to stablecoins for international supplier payments, so around $10,000/month.”
- “I’m liquidating my crypto holdings from another exchange over the next 3 months, approximately $100,000 total, withdrawing to my bank account.”
Bad Answers:
- “As much as possible.” ← Vague, doesn’t help risk assessment
- “It depends.” ← On what? Officer needs at least a rough range
- “I’ll see how it goes.” ← Not helpful for AML risk scoring
- MAJOR RED FLAG: “I’ll deposit $500,000/month” but declared source of funds is “$60k salary” ← Income-activity mismatch = potential money laundering
Question Category 3: Purpose of Using Crypto
Purpose: Distinguish between legitimate use (investment, payments) vs illicit (sanctions evasion, darknet purchases)
Officer: “What is your intended use of cryptocurrency? Investment, trading, payments, other?”
Good Answers:
- “Long-term investment. I believe in Bitcoin as a hedge against inflation.”
- “I’m a freelance graphic designer working with international clients. I use stablecoins to receive payments faster than wire transfers.”
- “I trade altcoins for profit. I pay taxes on capital gains annually.”
- “I’m exploring DeFi protocols for yield farming. I understand the risks.”
Bad Answers (Red Flags):
- “To move money out of [sanctioned country].” ← Sanctions evasion
- “I don’t trust banks, crypto is untraceable.” ← Misunderstanding + possible illicit intent
- “For privacy reasons.” ← While legitimate privacy exists, phrased this way raises AML concerns
- “I can’t tell you.” ← Immediate red flag for compliance
Question Category 4: Previous Crypto Experience
Purpose: Cross-check user’s story, identify potential account suspension history at other exchanges
Officer: “Have you used other cryptocurrency exchanges before? Which ones?”
Good Answers:
- “Yes, I’ve been using [Coinbase/Binance/Kraken] for 3 years. No issues with my account.”
- “No, this is my first crypto account. I’m new to cryptocurrency.”
- “I previously used [Exchange X], but I’m switching to your platform because of lower fees / better features.”
Bad Answers:
- “My account was banned at [Exchange X].” ← Officer will ask why (fraud? AML violation?)
- Lists 10+ exchanges in rapid succession ← Pattern of account-hopping (possible banned user creating new accounts)
- “I don’t remember.” ← If user is experienced trader, should remember major platforms
Question Category 5: Residence & Tax Status

Purpose: Verify user is not from restricted jurisdiction (sanctioned country, US if exchange not licensed there)
Officer: “Where do you currently reside? What is your citizenship/tax residency?”
Good Answers:
- “I live in [City, Country]. I’m a citizen and tax resident there.”
- “I’m a US citizen living in Singapore. I file taxes in both countries.”
- “I was born in [Country A] but now live in [Country B] permanently. Here’s my residence permit.”
Bad Answers (Red Flags):
- IP mismatch: User says “I live in UK” but IP address shows connection from Iran (sanctioned country using VPN)
- “I travel a lot, no fixed address.” ← Difficult to assess jurisdiction, compliance risk
- “I’m from [sanctioned country] but using a friend’s account.” ← Straw man account violation
- Refuses to answer ← Cannot complete EDD without jurisdiction disclosure
Additional Questions for High-Net-Worth / Institutional Accounts:
If user is depositing $1M+:
- “Are you investing on behalf of anyone else, or is this account solely for your personal use?” (Checking for beneficial ownership)
- “Does your employer know you’re making these transactions?” (If funds from business)
- “Will you be receiving funds from third parties, or only depositing your own funds?” (Third-party payment red flag)
For Business Accounts:
- “What is your business entity type? LLC, corporation, sole proprietorship?”
- “Who are the beneficial owners (individuals owning 25%+ equity)?”
- “Do you have an AML compliance officer within your company?”
Red Flags Compliance Officers Watch For:
During the interview, officers are trained to detect:
- Scripted answers: Sounds like reading from a prepared document (possible coached fraud)
- Excessive nervousness: Sweating, avoiding eye contact, long pauses (cultural context important—some cultures less direct eye contact)
- Inconsistencies: Says “I’m a doctor” but documents show warehouse worker employment
- Evasive responses: Deflects questions, gives non-answers
- Overconfidence: “I know all the rules, I’ve done this before” (experienced fraudster?)
- Impatience: Rushes officer, demands immediate approval (urgency = potential scam)
How Long This Takes:
- Low-risk case (clear source of funds, consistent story): 10 minutes
- High-risk case (large amounts, complex business structure): 20-30 minutes
Step 4: Post-Call Review & Decision (24-48 hours after call)
What Happens After Call Ends:
Immediate Actions (First hour):
- Compliance officer completes internal Risk Assessment Form:
- Identity verification confidence: Pass / Fail / Unclear
- Source of funds credibility: High / Medium / Low
- Transaction pattern risk: Low / Medium / High
- Sanctions/PEP screening result: Clear / Hit (requires escalation)
- Overall recommendation: Approve / Reject / Request Additional Info
Decision Criteria:
APPROVE Account (if all conditions met):
- Identity confirmed with 95%+ confidence (face match, liveness passed)
- Source of funds documented and credible (pay stubs, business docs, tax returns)
- No sanctions/PEP hits OR PEP status acceptable (not high-risk political office)
- Responses consistent with submitted documents
- No red flags in blockchain wallet analysis (if applicable)
REQUEST ADDITIONAL INFO (if gaps exist):
- Identity verification slightly unclear (old photo, need updated ID)
- Source of funds partially documented (need more bank statements, employment verification)
- Minor inconsistencies that can be resolved (name spelling variation, old address on utility bill)
REJECT Account / SUSPEND Indefinitely (if major red flags):
- Failed identity verification (suspected fake ID, face mismatch, deepfake detected)
- Unverifiable source of funds (vague answers, no documentation, income-transaction mismatch)
- Sanctions hit (OFAC list match, country ban)
- High-risk PEP (active government official in corruption-prone jurisdiction)
- Suspicious activity patterns (wallet linked to mixing services, darknet markets, ransomware)
- If rejected for fraud/sanctions: Exchange files Suspicious Activity Report (SAR) with FinCEN (US) or equivalent FIU (Financial Intelligence Unit) in other jurisdictions
Data Storage & Retention:
Where KYC Data Is Stored (NOT on blockchain):
- Encrypted Data Vaults (EDV): Secure databases with AES-256 encryption
- Access Controls: Only authorized compliance officers with multi-factor authentication can view
- Retention Period:
- US (FinCEN): 5 years after account closure
- EU (GDPR): 5-10 years (varies by member state AML laws)
- UK (FCA): 5 years after end of business relationship
- Backup Systems: Redundant storage (AWS, Google Cloud) in multiple geographic regions for disaster recovery
What About “On-Chain KYC”?
- Current Reality (2025): Most exchanges do NOT store KYC data on public blockchains due to:
- Privacy laws: GDPR “right to erasure” conflicts with blockchain immutability (can’t delete data from blockchain)
- Liability risk: Data breach exposes identity docs to entire world permanently
- No regulatory requirement: FinCEN, MiCA, FCA do NOT mandate blockchain-based KYC
- Experimental Use Cases: Some projects use:
- On-chain attestations: Cryptographic proof that “User X passed KYC with Provider Y” (no personal data stored, just boolean: verified=true)
- Hashed identifiers: Store cryptographic hash of documents (not documents themselves) for proof of existence
- Permissioned blockchains: Private ledgers visible only to authorized parties (banks, exchanges)
- Bottom Line: “On-chain KYC” is mostly theoretical/pilot phase in 2025. Standard practice is centralized encrypted databases.

User Notification Timeline:
Scenario 1: APPROVED
- Timeline: 24-48 hours after call (sometimes same day if simple case)
- Email Subject: “Your [Exchange] Account Verification Complete”
- Email Content:
- “Good news! Your Enhanced Due Diligence verification has been approved.”
- “Your account is now fully verified. You can:”
- Deposit fiat currency (bank transfer, credit card)
- Trade all supported cryptocurrencies
- Withdraw up to [higher limits, e.g., $100,000/day]
- Access advanced features (margin trading, staking, earn products)
- Dashboard Status: Green checkmark “Verified” badge
Scenario 2: ADDITIONAL INFO NEEDED
- Timeline: 12-24 hours after call
- Email Subject: “Action Required: Additional Documents Needed”
- Email Content:
- “We’ve reviewed your verification call but need additional documentation:”
- “Please provide updated proof of address (your utility bill was dated 4 months ago, we need one within 3 months)”
- “Please upload 2 additional months of pay stubs to verify income”
- “Please clarify source of funds for [specific transaction]”
- “Respond within 7 days to avoid account restrictions.”
- “We’ve reviewed your verification call but need additional documentation:”
- Dashboard Status: Orange exclamation “Pending: Action Required”
Scenario 3: REJECTED
- Timeline: 24-72 hours after call (takes longer due to internal review + legal check before rejection)
- Email Subject: “Your [Exchange] Account Verification Update”
- Email Content (Careful Wording to Avoid Legal Liability):
- “After careful review, we’re unable to verify your account at this time.”
- “This decision is based on our risk management policies and regulatory obligations.”
- Specific reason usually NOT disclosed to avoid:
- Tipping off user if SAR was filed (illegal in US to disclose SAR)
- Legal disputes (“You called me a fraudster!”)
- Providing playbook for fraudsters to improve fake docs next time)
- “You may withdraw existing funds [if applicable] but cannot deposit or trade. Account will be closed in 30 days.”
- “This decision is final. Creating a new account is prohibited.”
- Dashboard Status: Red X “Verification Failed”
What If User Disagrees with Decision?
Appeal Process (Varies by Exchange):
- Some exchanges allow appeals:
- User submits written explanation + additional evidence
- Separate compliance officer reviews (not same person who made original decision)
- Final decision within 14 business days
- Most exchanges do NOT allow appeals for:
- Sanctions hits (OFAC list match = non-negotiable)
- Confirmed fraud (fake ID verified by forensic team)
- Regulatory prohibition (e.g., US citizen trying to use non-US-licensed exchange)
If Appeal Rejected:
- User must use different exchange (if eligible)
- Cannot create new account under different name (identity fraud)
- May need to work with compliance officer at new platform to explain previous rejection (if asked)
Data Retention & User Rights:
What Happens to Call Recording & Documents?
- Stored securely: Encrypted, access-logged (audit trail of who viewed data)
- Retention period: 5-10 years per AML laws (even if account closed)
- User rights (GDPR, CCPA):
- Right to access: User can request copy of their KYC data
- Right to rectification: User can correct errors (wrong address, spelling mistake)
- Right to erasure (“right to be forgotten”): User can request deletion AFTER retention period ends (not during 5-10 year window)
- Right to data portability: User can request KYC data in machine-readable format (to take to another exchange)
How to Request Your Data:
- Contact exchange support: “I’m requesting my KYC data under GDPR Article 15”
- Exchange must respond within 30 days (GDPR) or 45 days (CCPA)
- Receive: Copy of ID, proof of address, call transcript (possibly redacted), risk assessment notes

Security & Privacy Challenges
Risks in Centralized KYC Systems (And How Industry Responds)
Risk #1: Mass Data Breaches
The Threat:
- Centralized databases storing millions of users’ IDs, addresses, selfies = high-value target for hackers
- Single breach can expose entire user base (unlike decentralized storage where each user’s data separate)
Real Examples:
Ledger (Hardware Wallet Company, July 2020):
- What happened: Marketing database breached, exposing 272,000 customer records
- Data leaked: Names, postal addresses, phone numbers, email addresses
- Impact: Used for phishing attacks (“Your Ledger device needs update—click here”) and physical theft attempts (criminals knew addresses of crypto holders)
- Ledger’s response: Improved database segmentation, hired CISO, launched bounty program
- Source: Ledger official statement, security audit reports
Poly Network (DeFi Platform, August 2021):
- What happened: $610 million hack (later returned), but KYC data breach also occurred
- Data leaked: User IDs, transaction histories (no government IDs stored, as DeFi platform)
- Note: Highlights that even non-custodial platforms with minimal KYC face risks
Recent 2023-2025 Incidents (Unverified Claims):
- Binance (2023): Hacker forum post claimed 10,000 KYC documents available for sale (Binance denied breach, said docs were from old phishing attack)
- Coinbase (2024): No confirmed breach, but insider trading case revealed employees had broad access to user data
- Note: Always check exchange’s official statement—many “breach” claims are phishing scams
How Exchanges Mitigate:
- Database segmentation: PII (name, address) stored separately from financial data (transaction history)
- Encryption at rest: AES-256 for stored documents
- Encryption in transit: TLS 1.3 for data transfers
- Regular security audits: Annual penetration testing by third parties (CertiK, Quantstamp)
- Bug bounty programs: Pay hackers to find vulnerabilities before malicious actors do (e.g., Coinbase pays up to $250,000 per critical bug)
Risk #2: Insider Threats
The Threat:
- Employees with access to KYC database can steal data or sell to criminals
- Compliance officers, customer support, IT staff may have legitimate access but abuse it
Real Examples:
Coinbase (Internal Investigation, 2024):
- What happened: Employee accessed user accounts without authorization, shared info with external party
- Action taken: Employee terminated, criminal charges filed, Coinbase implemented stricter access controls
- Lesson: Even legitimate employees with access pose risk
Binance (Alleged, 2023):
- Claim: Ex-employee allegedly leaked 10,000 KYC docs
- Binance response: Denied breach, said docs were from 2019 phishing attack, not internal leak
- Ongoing: Investigation by security firms
How Exchanges Mitigate:
- Role-based access control (RBAC): Customer support sees name + account balance ONLY; compliance officers see full KYC docs
- Principle of least privilege: Grant minimum access needed for job function
- Access logging: Every data view logged with timestamp, employee ID, reason for access
- Regular audits: Review access logs quarterly for suspicious patterns (e.g., employee viewed 1,000 accounts in 1 day = red flag)
- Background checks: Enhanced screening for compliance team (credit checks, criminal records)
- Non-disclosure agreements (NDAs): Legal contracts with penalties for data misuse
Risk #3: Regulatory Penalties for Breaches
The Threat:
- GDPR (EU), CCPA (California), other privacy laws impose heavy fines for inadequate data protection
Real Penalties:
Revolut (Lithuania, April 2025):
- Violation: “Persistent shortcomings” in AML prevention, inadequate KYC procedures
- Fine: €3.5 million
- Reason: Rapid growth (millions of users added) without scaling compliance team, resulting in weak verification
- Source: Lithuanian regulatory authority press release
Barclays (UK, July 2025):
- Violation: Failed to gather sufficient KYC info, inadequate transaction monitoring
- Fine: £42 million (approx $53 million USD)
- Context: Traditional bank, but lesson applies to crypto—regulators don’t accept “we grew too fast” as excuse
- Source: UK FCA enforcement notice
GDPR Data Breach Penalties (EU):
- Maximum fine: €20 million OR 4% of global annual revenue, whichever is HIGHER
- Examples:
- British Airways (2020): £20 million for customer data breach (originally £183M, reduced on appeal)
- Marriott (2020): £18.4 million for breach exposing 339 million guest records
- Note: No major crypto exchange has faced maximum GDPR fine yet, but risk exists
How Exchanges Mitigate:
- SOC 2 Type II certification: Annual audit proving security controls (access management, encryption, incident response)
- Cyber insurance: Policies covering breach costs (notification, credit monitoring for victims, legal fees)
- Incident response plan: Pre-written playbook for breach scenarios (within 72 hours of discovery, notify users + regulators per GDPR)
- Data minimization: Store only required KYC data (don’t collect social security numbers if not legally needed)
- Regular deletion: Purge accounts after retention period ends (5-10 years) to reduce exposure
Industry Shift: Moving AWAY from Centralized Storage (Slowly)
Current Reality (2025):
- 95%+ exchanges still use centralized encrypted databases (regulatory requirement, proven technology)
- Decentralized alternatives (SSI, on-chain KYC) in pilot phase only
Experimental Approaches:
1. Self-Sovereign Identity (SSI) Pilots:
- What: Users store KYC docs in their own digital wallet (phone app), share cryptographic proof with exchanges
- Status: EU eIDAS 2.0 pilots, Japan Digital Agency testing with My Number ID
- Adoption: <1% of crypto users have SSI credentials in 2025
- Regulatory acceptance: NOT approved as substitute for traditional KYC by US regulators (FinCEN, SEC, CFTC)
2. Zero-Knowledge Proofs (ZKP) for Selective Disclosure:
- What: Prove “I am over 18” or “I am not from sanctioned country” without revealing exact birthdate or location
- Status: Experimental (Polygon ID, zkMe protocols)
- Limitation: Regulators require full document verification, not just boolean proofs
3. Federated KYC (Shared Verification Across Exchanges):
- What: User verifies once with KYC provider (Jumio, Onfido), receives cryptographic credential accepted by multiple exchanges
- Status: Some adoption (Sumsub, KYC-Chain used by multiple platforms)
- Challenge: Liability (who’s responsible if credential is fraudulent?)
Timeline for Mainstream Adoption:
- 2025-2026: Continued pilots, no major regulatory approvals
- 2027-2028: Possible EU regulatory framework for SSI (if eIDAS 2.0 pilots succeed)
- 2030+: Potential mainstream adoption (not guaranteed)
Bottom Line for Users & Exchanges Today:
- Use centralized KYC with encrypted storage, access controls, audits (compliant, proven)
- Don’t rely on SSI/ZKP alone (not regulatory-approved in 2025)
- Monitor innovation (may become option in 5+ years)
Privacy Concerns in Crypto
- Loss of anonymity for traders.
- Risk of third-party misuse of sensitive data.

Breach Case Examples
- Coinbase breach: Insider attack exposed IDs, addresses, and financial info.
- Binance incident: Hacker forum leaks claimed access to user KYC data.
Case Studies: Failures & Improvements
Case Study #1: Ledger Data Breach (July 2020)
What Happened:
Background:
- Ledger = hardware wallet manufacturer (not crypto exchange, but stores customer KYC-like data)
- Marketing database hacked, exposing 272,000 customer records
- Attacker accessed: Names, postal addresses, phone numbers, email addresses, order details
- No financial data or crypto holdings compromised (Ledger devices remained secure)
Timeline:
- June 2020: Initial breach occurred (Ledger unaware)
- July 14, 2020: Ledger discovered unauthorized access to e-commerce database
- July 29, 2020: Ledger published security incident report, notified 9,500 users with detailed data exposed
- December 2020: Full database (272,000 records) leaked on hacker forum RaidForums
- 2021-2023: Victims reported physical threats, phishing attacks, SIM-swapping attempts
Impact on Users:
Phishing Campaigns:
- Attackers sent emails: “Your Ledger device has been compromised”
- Fake Ledger websites collecting seed phrases (12-24 word recovery keys)
- Estimated $10M+ stolen via phishing (users entered seed phrases on fake sites)
Physical Security Threats:
- Criminals knew exact addresses of crypto holders
- Multiple reports of:
- Threatening letters: “We know you own crypto. Pay $5,000 BTC or we’ll target your family.”
- Home invasion attempts (rare, but occurred in at least 3 documented cases)
- “Wrench attacks” (physical coercion to reveal seed phrases)
Long-Term Consequences:
-
- Victims’ data STILL circulating on dark web in 2025 (5 years later)
- Ongoing phishing campaigns targeting Ledger customers
- Class-action lawsuit filed (settled for undisclosed amount)
Case Study #2: Coinbase Insider Threat (2024)
What Happened:
Incident:
- Coinbase employee accessed user accounts without authorization
- Shared confidential customer information with external party (identity not disclosed)
- Detected by Coinbase’s internal monitoring systems
Timeline:
- Q1 2024: Employee began unauthorized access (exact start date not public)
- Q2 2024: Coinbase security team flagged unusual account access patterns
- June 2024: Internal investigation launched
- July 2024: Employee terminated, criminal charges filed with FBI
- August 2024: Coinbase notified affected users, offered free credit monitoring
Scale:
- Number of affected accounts: Not disclosed (Coinbase cited ongoing investigation)
- Type of data accessed: Customer names, balances, transaction histories (no passwords or 2FA codes compromised)
What This Reveals About Insider Threats:
Why Insiders Are Dangerous:
- Legitimate access: Compliance officers, customer support, IT staff need to view user data for job functions
- Hard to detect: Unlike external hackers, insiders use authorized credentials (no brute-force alerts)
- High-value targets: Disgruntled employees, those with financial stress, or bribed by external actors
Common Insider Threat Scenarios in Crypto:
- Data theft for sale: Employee exports KYC database, sells on dark web ($10-50 per ID document)
- Account manipulation: Customer support changes withdrawal address to attacker’s wallet
- Information for phishing: Employee leaks user emails/phone numbers to phishing gangs
- Espionage: Competitor bribes employee for trading data, user behavior analytics
How Coinbase Detected & Responded:
Detection Mechanisms:
- Access logging: Every customer account view logged with employee ID, timestamp, reason
- Anomaly detection: AI flagged unusual pattern (employee viewed 500+ accounts in 1 week, normal is 10-20)
- Peer comparison: System compared employee’s access to colleagues in same role (outlier = red flag)
- Audit trails: Quarterly manual reviews of high-privilege accounts (compliance officers, admins)
Response Actions:
- Terminated employee immediately (escorted from building same day)
- Revoked all system access, disabled credentials
- Forensic investigation: Reviewed every account accessed, every file downloaded
- Filed criminal complaint with FBI (insider trading, unauthorized access to computer systems)
- Notified affected users within 30 days (GDPR/CCPA compliance)
- Offered 2 years free credit monitoring (standard post-breach mitigation)
Improvements Implemented Post-Incident:
- Break-glass procedures: High-risk actions (viewing whale accounts >$1M) require two-person approval
- Randomized audits: 10% of employee access logs randomly audited weekly (not just quarterly)
- Behavioral analytics: Machine learning models predict insider threat risk based on access patterns + HR flags (recent disciplinary action, failed performance review)
- Data minimization: Customer support sees only transaction ID, not full name/address unless needed for specific ticket
Lessons for Crypto Industry:
1. Principle of Least Privilege:
- Bad: All customer support agents can view full KYC documents
- Good: Tier 1 support sees name + account balance only; Tier 2 (escalations) sees full KYC; Compliance officers only group with unrestricted access
2. Access Monitoring:
- Bad: Log access but never review logs (security theater)
- Good: Automated anomaly detection + weekly random audits + quarterly full reviews
3. Background Checks & Ongoing Monitoring:
- Pre-employment: Credit checks, criminal records (financial stress = insider threat risk)
- During employment: Monitor for red flags (sudden lifestyle changes, resentment, frequent access to accounts of high-net-worth users)
4. Separation of Duties:
- Bad: Same person who onboards users can also approve withdrawals
- Good: Onboarding team ≠ Operations team ≠ Compliance team (checks and balances)
5. Culture of Security:
- Regular security training: “What to do if bribed,” “How to report suspicious colleague”
- Whistleblower protection: Anonymous hotline for reporting insider threats
- Exit interviews: When employee leaves, immediate credential revocation + review of all recent activity
Case Study #3: Positive Example – Kraken’s Proof of Reserves (Ongoing)
What They Did Right:
Background:
- After FTX collapse (Nov 2022) exposed customer fund misuse, exchanges needed to prove solvency
- Kraken implemented Proof of Reserves (PoR) + transparency measures
Key Practices:
1. Merkle Tree Verification (Cryptographic Proof of Reserves):
- Users can verify their balance is included in Kraken’s total reserves
- Process:
- Kraken publishes cryptographic hash of all user balances
- Each user receives individual hash (their balance + salt)
- User verifies their hash is part of published Merkle tree
- Ensures Kraken cannot fabricate reserves (math doesn’t work if they lie)
2. Third-Party Audits:
- Independent auditors (Armanino LLP) verify on-chain reserves match user deposits
- Published quarterly (not just one-time PR stunt)
- Audits cover: Bitcoin, Ethereum, USDT, USDC, and 100+ other assets
3. Transparent Communication:
- Blog posts explaining PoR methodology (not just “trust us”)
- Open-source tools for users to verify their inclusion
4. KYC Security Measures:
- SOC 2 Type II certified (annual audits of data security controls)
- Bug bounty program: $100-$100,000 for security vulnerabilities
- Regular security training for employees (phishing simulations, insider threat awareness)
Why This Matters for KYC:
Trust Through Transparency:
- Users more willing to submit KYC if they trust exchange’s security practices
- PoR doesn’t directly relate to KYC, but demonstrates overall operational integrity
Best-in-Class Security Culture:
- If exchange invests heavily in reserves transparency, likely also invests in KYC data protection
- Red flag: Exchange that refuses audits probably has other skeletons (lax KYC, weak AML, fractional reserves)
Regulatory Confidence:
- Exchanges with strong compliance (including KYC) + financial transparency = lower regulatory risk
- Easier to obtain banking partnerships, fiat on-ramps, licenses in new jurisdictions
Lessons for Users:
Choose exchanges with:
- SOC 2 Type II or ISO 27001 certification (proves security controls)
- Public security audits (penetration tests, bug bounties)
- Transparent incident response (if breach occurs, they disclose promptly, not hide)
- Clear privacy policy (what KYC data stored, how long, who can access)
Avoid exchanges that:
- Refuse third-party audits (“proprietary reasons”)
- Have history of breaches with poor response (delayed notification, blamed users)
- No clear terms of service / privacy policy
- Anonymous team (no one to hold accountable)
Innovations in KYC Verification Calls
Innovation #1: Advanced Biometric Authentication (Current Technology, 2025)
What’s Being Used Today:
1. Facial Recognition (Most Common):
How It Works in KYC Calls:
- User holds ID to camera → Officer captures photo of ID
- User performs liveness check (blink, turn head, smile)
- AI software extracts facial landmarks from both:
- ID photo (2D image)
- Live video (3D face mapping using depth sensors if available, or motion analysis)
- Compares key features:
- Distance between eyes, nose width, jawline shape, cheekbone structure
- Generates similarity score: 0-100% match
Technology Providers:
- Onfido: AI-powered document + face verification (used by Revolut, Coinbase)
- Jumio: Liveness detection + face match (used by Airbnb, Uber, multiple crypto exchanges)
- Sumsub: Biometric verification with anti-spoofing (used by Bybit, multiple DeFi platforms)
Accuracy Rates (2025 Industry Standards):
- True Accept Rate (TAR): 98-99.5% (legitimate users correctly matched)
- False Accept Rate (FAR): 0.01-0.1% (fraudsters incorrectly accepted)
- False Reject Rate (FRR): 0.5-2% (legitimate users incorrectly rejected due to poor lighting, aged ID photo)
Anti-Spoofing Techniques:
- Attack: Photo of a photo (print ID photo, hold to camera)
- Defense: Liveness detection (blinking, head movement impossible with static photo)
- Attack: Pre-recorded video
- Defense: Random prompts (officer asks unexpected action like “touch your nose,” can’t be pre-recorded)
- Attack: Deepfake video (AI-generated face)
- Defense: Texture analysis (deepfakes have unnatural skin texture, lighting inconsistencies), micro-expression detection (real faces have subtle involuntary movements, deepfakes don’t)
- Attack: 3D mask (silicone mask of real person’s face)
- Defense: Infrared sensors detect heat patterns (real skin vs silicone), depth mapping (mask doesn’t have natural facial contours)
2. Voice Biometrics (Emerging in Crypto KYC):
How It Works:
- During KYC call, user speaks (answers questions)
- Software analyzes voice characteristics:
- Pitch: Frequency of vocal cords
- Tone: Voice quality, timbre
- Cadence: Speaking rhythm, pace
- Accent markers: Regional pronunciation patterns
- Creates unique “voiceprint” (like fingerprint, but for voice)
- Compares to future calls: If same user calls back, voice should match
Use Cases:
- Initial verification: Confirm user is not using voice-changing software
- Re-verification: If user loses 2FA device, calls support to regain access → voice biometric confirms identity
- Fraud prevention: Detect if someone else (family member, attacker) using account
Technology Providers:
- Nuance (Microsoft): Used by banks for phone banking authentication
- Pindrop: Detects spoofed calls, synthetic voices
- VoiceVault: Multi-factor authentication with voice biometrics
Accuracy:
- Equal Error Rate (EER): 1-2% (point where false accept = false reject)
- Better than passwords: Voice harder to steal than password/PIN
Limitations:
- Environmental noise (background music, traffic) reduces accuracy
- Illness (cold, sore throat) changes voice temporarily
- Aging (voice changes over years, requires re-enrollment)
- Privacy concerns (voice data = sensitive biometric, GDPR requires explicit consent)
3. Behavioral Biometrics (Cutting-Edge, Limited Adoption):
What It Is:
Analysis of HOW user interacts with device during KYC process:
-
- Typing patterns: Speed, rhythm, pressure when entering info
- Mouse movements: Speed, trajectory, click patterns
- Touchscreen gestures: Swipe speed, finger pressure (mobile)
- Device angle: How user holds phone during selfie
How It Detects Fraud:
- Fraudster using stolen documents will have different behavioral patterns than legitimate user
- Example: Legitimate user fills out form calmly, fraudster rushes (nervous, trying to submit before detection)
Technology Providers:
- BioCatch: Behavioral biometrics for fraud detection (used by banks)
- Keyless: Biometric authentication without passwords
Current Status in Crypto (2025):
- Experimental: <5% of crypto exchanges use behavioral biometrics for KYC
- More common: Used for transaction fraud detection (unusual trading patterns)
Limitations:
- High false positive rate (elderly users type slowly, doesn’t mean fraud)
- Privacy concerns (continuous monitoring feels invasive)
- Requires large dataset to establish baseline (doesn’t work for first-time users)
Privacy & Ethical Concerns with Biometrics:
GDPR/CCPA Compliance:
- Biometric data = “special category” under GDPR (sensitive personal data)
- Requires:
- Explicit consent (cannot be implied, must be opt-in with clear language)
- Purpose limitation (can only use for stated purpose, not repurpose later)
- Data minimization (store only necessary biometric data)
- Right to erasure (user can request deletion after account closure)
Storage Risks:
- Danger: Centralized biometric database = high-value target for hackers
- Unique problem: Passwords can be reset; biometrics cannot (your face is permanent)
- Mitigation: Some systems store biometric templates (mathematical representation) not raw images (templates harder to reverse-engineer)
Bias & Discrimination:
- Early facial recognition systems had higher error rates for:
- Non-white faces (trained on predominantly white datasets)
- Women (trained on predominantly male faces)
- Elderly (age progression not accounted for)
- Industry response (2020-2025): Diversified training datasets, regular bias audits, transparency reports
Surveillance Concerns:
- Biometric data could be shared with governments (law enforcement requests)
- Mission creep (KYC biometrics used for advertising, user tracking)
- Best practice: Exchanges should commit to NOT sharing biometric data except where legally required (court orders, AML investigations)
Innovation #2: Self-Sovereign Identity (SSI) – Future Technology, Pilot Phase Only

CRITICAL DISCLAIMER – READ FIRST:
Regulatory Reality Check (2025):
- US regulators (FinCEN, SEC, CFTC) have NOT approved SSI as substitute for traditional KYC
- <1% of crypto exchanges accept SSI credentials in 2025
- Pilot phase only: EU eIDAS 2.0, Japan Digital Agency testing
- Mainstream adoption: 2027-2028 earliest (IF pilots succeed, not guaranteed)
- Today’s requirement: Exchanges MUST use centralized KYC with document verification, encrypted storage, record retention per FinCEN/FATF
Bottom Line: SSI is promising technology for the FUTURE, but cannot replace traditional KYC for regulatory compliance in 2025.
What Is Self-Sovereign Identity (SSI)?
Concept:
- Users control their own identity data (documents, credentials) instead of relying on centralized authorities (government, exchanges, banks)
- Identity stored in user’s digital wallet (smartphone app, hardware device)
- Users selectively share credentials with verifiers using cryptographic proofs
Key Components:
1. Decentralized Identifiers (DIDs):
- Unique ID not controlled by any central authority
- Format:
did:example:123456789abcdefghi(like a URL, but for identity) - Anchored on blockchain (Ethereum, Polygon, Hyperledger Indy) for tamper-proof verification
- User owns private keys; only they can update/revoke DID
2. Verifiable Credentials (VCs):
- Digital attestations issued by trusted parties (government, university, employer, KYC provider)
- Examples:
- Government issues: “This person is over 18” (age credential)
- KYC provider issues: “This person passed identity verification on [date]” (KYC credential)
- University issues: “This person graduated with Computer Science degree in 2020”
- Cryptographically signed by issuer (can’t be forged)
- Stored in user’s wallet, not issuer’s database
3. Zero-Knowledge Proofs (ZKPs):
- Cryptographic technique: Prove you possess information without revealing the information
- Example: Prove “I am over 18” without revealing exact birthdate
- How it works (simplified):
- User’s wallet generates cryptographic proof: “Birthdate is before 2007”
- Verifier (exchange) checks proof cryptographically
- Result: TRUE/FALSE, but verifier never sees actual birthdate
How SSI Would Work for Crypto KYC (Theoretical):
Step 1: User Gets Verified Once (With Trusted KYC Provider):
- User visits KYC provider (Onfido, Sumsub, government agency)
- Submits documents (ID, proof of address, selfie)
- KYC provider verifies identity
- Issues Verifiable Credential (VC) to user’s digital wallet:
- “User [DID] verified by [KYC Provider] on [Date]”
- “Verification level: Full KYC (ID + address + biometric)”
- Cryptographically signed by KYC provider
Step 2: User Signs Up at Crypto Exchange:
- Instead of uploading documents again, user presents VC from wallet
- Exchange verifies:
- VC signature is valid (KYC provider really issued this)
- VC not expired or revoked
- User controls DID (proves ownership with private key)
- Exchange accepts VC as proof of identity (no need to re-upload ID)
Step 3: Ongoing – User Controls Data:
- User can revoke access if exchange misuses data
- User updates credentials in wallet (moved to new address? Update proof of address VC)
- User takes credentials to new exchange (portable identity)
Benefits of SSI (If It Were Widely Adopted):
1. Privacy:
- Exchange doesn’t store raw ID documents (only cryptographic proof user was verified)
- Reduced breach risk (no centralized database of IDs to hack)
- Selective disclosure (user shares only necessary info: age verification but not exact birthdate)
2. User Control:
- Users own their data, can revoke access
- Portable credentials (verify once, use everywhere)
- Transparency (user sees exactly what data shared with each verifier)
3. Cost Efficiency for Exchanges:
- Reduced KYC costs (no need to re-verify user if they present valid VC from trusted provider)
- Faster onboarding (instant verification if VC valid)
- Less data storage liability (don’t hold user documents)
Current Limitations & Challenges (Why Not Mainstream in 2025):
1. Regulatory Acceptance:
- US regulators require exchanges to independently verify users, maintain records
- FinCEN: “Reliance on third-party KYC must include due diligence on provider” (exchanges can’t blindly trust VCs)
- FATF: Requires “reliable, independent source documents” for CDD (VC alone may not satisfy)
- Bottom line: Even if user has VC, exchange may still need to verify documents to satisfy regulators
2. Standardization Gaps:
- Multiple competing SSI frameworks: Sovrin, uPort, Polygon ID, Dock.io (no universal standard yet)
- Interoperability issues (VC issued by Sovrin may not work with uPort wallets)
- W3C standards (DIDs, VCs) exist but implementation varies widely
3. Trust in Issuers:
- Exchange must trust the KYC provider who issued VC (What if provider has low verification standards?)
- Liability question: If fraudster uses fake VC, who’s responsible? User? Issuer? Exchange?
- Revocation challenges (if user becomes sanctioned, how do all exchanges know to revoke VC?)
4. User Experience:
- Most users don’t understand SSI (need to manage private keys, understand wallets)
- Key loss = identity loss (no “reset password” for private keys)
- Complexity (easier to just upload ID again than set up SSI wallet)
5. Technical Scalability:
- Blockchain verification can be slow (Ethereum network congestion)
- Cost (blockchain transaction fees for DID anchoring, VC issuance)
Current SSI Pilots (2025):
European Union – eIDAS 2.0:
- What: EU regulation for electronic identification and trust services
- Status: Pilot phase, aiming for SSI-compatible digital identity wallets by 2026
- Scope: Government IDs, driver’s licenses, health records, educational diplomas
- Crypto relevance: Could issue “EU citizen” credential, but NOT replacement for full KYC (exchanges still need proof of address, source of funds)
Japan – Digital Agency My Number Integration:
- What: Exploring blockchain-based credentials for national ID (My Number)
- Investment: ¥20 billion (~$200M USD) for SSI infrastructure
- Partners: NTT Data, Sony developing SSI systems for employees, citizens
- Status: Internal corporate use cases (employee IDs), not yet public-facing crypto KYC
United States – Limited Pilots:
- DHS (Department of Homeland Security): Tested SSI for border crossing (traveler credentials)
- States (IL, WY): Exploring digital driver’s licenses with SSI principles
- Crypto: NO federal endorsement of SSI for crypto KYC (FinCEN still requires traditional methods)
Industry Initiatives:
- Civic: SSI platform for identity verification (partnerships with some crypto projects)
- Polygon ID: Privacy-preserving identity on Polygon blockchain
- Dock.io: Verifiable credential platform (used by some HR, education platforms, not mainstream crypto)
Realistic Timeline for SSI in Crypto KYC:
2025-2026: Continued Pilots
- More exchanges experiment with SSI for low-risk tiers (e.g., withdrawal limits <$1,000/day)
- Regulatory sandboxes (UK FCA, Singapore MAS) test SSI compliance
2027-2028: Possible Regulatory Frameworks
- IF EU eIDAS 2.0 pilots succeed → EU may approve SSI for certain KYC requirements
- US: Unlikely before 2028 (regulatory inertia, focus on stablecoin regulation first)
2030+: Mainstream Adoption (Optimistic Scenario)
- SSI becomes option for exchanges (not replacement, but supplement to traditional KYC)
- Users with government-issued SSI credentials can fast-track verification
- Exchanges still maintain traditional KYC for users without SSI
Alternative Scenario: SSI Remains Niche
- Regulatory concerns persist (liability, trust in issuers)
- User adoption low (too complex, key management fears)
- Centralized KYC with encryption remains dominant
What This Means for Users & Exchanges TODAY:
For Users:
- Don’t wait for SSI to use crypto (it’s 5+ years away minimum)
- Complete traditional KYC with exchanges using encrypted storage, SOC 2 certified
- Monitor SSI developments, but don’t rely on it for immediate access
For Exchanges:
- Maintain compliant centralized KYC (FinCEN, MiCA requirements)
- Participate in SSI pilots IF in regulatory sandbox (UK FCA, Singapore MAS)
- Don’t abandon traditional KYC for SSI alone (regulatory violation)
IMPORTANT: Current State of SSI Adoption (2025)
While SSI technology is mature (W3C standards established, multiple frameworks operational), regulatory acceptance remains
LIMITED: Technology ready: Decentralized Identifiers (DIDs), Verifiable Credentials, Zero-Knowledge Proofs are production-ready
Regulatory pilots only:
- EU: Exploring SSI via eIDAS 2.0 and EBSI (European Blockchain Services Infrastructure) – pilot phase
- US: SEC, FinCEN, CFTC have NOT approved SSI as substitute for traditional KYC
Mainstream adoption low: <1% of crypto exchanges accept SSI credentials in 2025
Realistic timeline:
- 2025-2026: Continued EU pilots
- 2027-2028: Potential regulatory frameworks emerge IF pilots succeed
- 2030+: Possible mainstream adoption (not guaranteed)
BOTTOM LINE: Crypto exchanges MUST maintain compliant centralized KYC today. SSI is promising for the future, but cannot replace traditional verification methods for regulatory compliance in 2025.
Reusable KYC Proofs
- Verified credentials on-chain used across multiple platforms without re-submission.
- Reduces data duplication and storage cost.
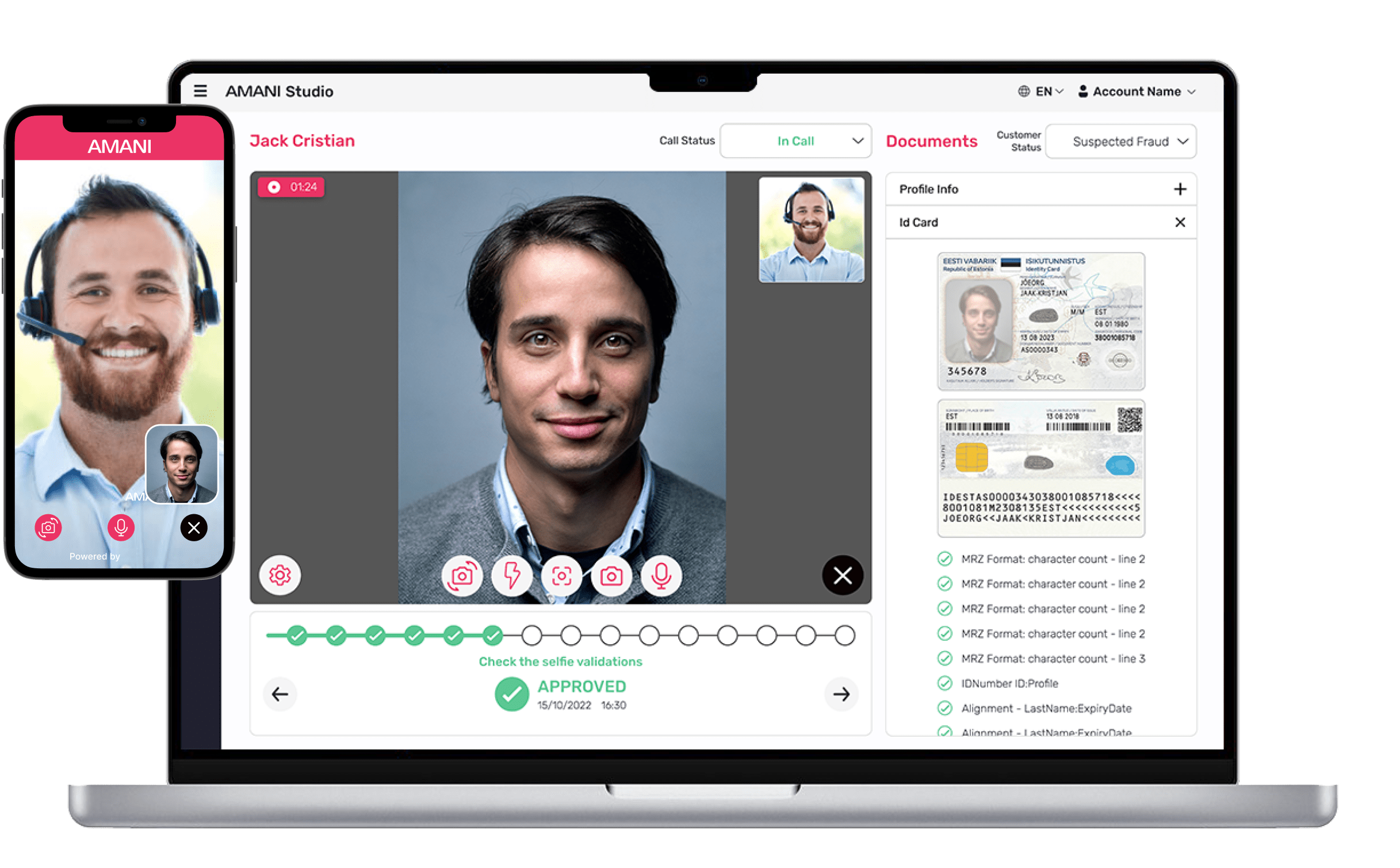
Best Practices for Crypto Exchanges Implementing KYC Calls
1. Risk-Based Approach (FATF Recommendation 1)
Principle:
- Don’t use same KYC process for all users (waste of resources)
- Tier verification based on risk factors
Implementation:
Tier 1 – Low Risk (95% of users):
- Automated eKYC: ID upload + selfie + address verification
- No call required
- Time: 5-20 minutes
- Cost: $0.50-2.00
- Example: Retail traders, deposits <$10,000/month
Tier 2 – Medium Risk (3-4% of users):
- Manual document review (compliance officer checks, no call)
- Triggered by: Unclear documents, minor inconsistencies
- Time: 1-2 business days
- Cost: $5-15
- Example: Aged ID photo, address mismatch (old utility bill)
Tier 3 – High Risk (<1-2% of users):
- Enhanced Due Diligence (EDD) with verification call
- Triggered by: PEP status, high-risk jurisdiction, large transaction volumes, suspicious patterns
- Time: 1-3 business days
- Cost: $15-30
- Example: Political official, user from sanctioned country, $100,000+ monthly volume
Regulatory Compliance:
- FATF Recommendation 1: “Apply risk-based approach to CDD”
- FinCEN guidance: “Risk assessment should consider customer type, products, geographic locations”
- Don’t apply EDD to everyone (disproportionate, wastes resources, poor user experience)
2. Data Security & Storage
Encryption Requirements:
At Rest (Stored Data):
- Use AES-256 encryption for all KYC documents
- Separate encryption keys from data (stored in Hardware Security Modules – HSMs)
- Encrypt call recordings, transcripts, biometric data
- Don’t store passwords/encryption keys in same database as encrypted data
In Transit (Data Transfer):
- Use TLS 1.3 for all data transfers (upload, download, API calls)
- Certificate pinning for mobile apps (prevent man-in-middle attacks)
- Don’t allow unencrypted HTTP connections
Database Segmentation:
- Store PII (name, address) separately from financial data (balances, transactions)
- Separate KYC documents from operational databases
- Rationale: If operational database breached, KYC docs still protected
Access Controls:
- Role-Based Access Control (RBAC):
- Customer support: See name + account balance only
- Compliance officers: Full KYC access
- IT staff: No access to production KYC data (only encrypted backups for disaster recovery)
- Multi-Factor Authentication (MFA) for all employees accessing KYC systems
- Access logging: Every document view logged with employee ID, timestamp, reason
- Quarterly audits: Review access logs for anomalies (employee viewed 1,000+ accounts = red flag)
Retention & Deletion:
- Retain KYC data per regulatory requirements:
- US (FinCEN): 5 years after account closure
- EU (GDPR): 5-10 years (varies by member state)
- UK (FCA): 5 years after end of business relationship
- Automated deletion after retention period (don’t hold data indefinitely)
- Secure deletion: Overwrite data multiple times (not just “delete file” which can be recovered)
3. Third-Party Audits & Certifications
SOC 2 Type II (Minimum Standard for Crypto Exchanges):
- What: Audit of security controls (access management, encryption, incident response)
- Frequency: Annual
- Provider: Big 4 accounting firms (Deloitte, PwC, EY, KPMG) or specialized firms (A-LIGN, Prescient Assurance)
- Cost: $15,000-$100,000 depending on exchange size
- Benefit: Proves to users, regulators, partners that security controls in place
ISO 27001 (International Standard for Information Security):
- What: Comprehensive information security management system (ISMS)
- Scope: All data, not just KYC (but KYC included)
- Frequency: Annual surveillance audits, full re-certification every 3 years
- Benefit: Global recognition, higher standard than SOC 2
Penetration Testing:
- What: Ethical hackers attempt to breach systems
- Frequency: Quarterly for production systems, annually for full audit
- Providers: CertiK, Trail of Bits, Halborn, Quantstamp
- Scope: Web application, API, database, network infrastructure
- Deliverable: Report with vulnerabilities, risk ratings, remediation steps
Bug Bounty Programs:
- What: Pay external security researchers to find vulnerabilities
- Platforms: HackerOne, Bugcrowd, Immunefi (crypto-focused)
- Rewards: $100-$250,000 depending on severity (Coinbase pays up to $250k for critical bugs)
- Benefit: Crowdsourced security, find vulnerabilities before malicious hackers
4. Compliance Officer Training
Who Conducts KYC Calls:
- Dedicated compliance officers (NOT customer support reps)
- Background checks: Credit check, criminal record (financial stress = insider threat risk)
- Minimum qualifications: CAMS (Certified Anti-Money Laundering Specialist) or equivalent
Training Requirements:
Initial Training (Before Conducting Calls):
- AML regulations: BSA, FATF, MiCA, local laws
- Red flag identification: Suspicious behavior, inconsistencies, fraud indicators
- Interview techniques: Open-ended questions, follow-up probes
- Cultural sensitivity: Name conventions (patronymics, multiple surnames), direct vs indirect communication styles
- Technology: How to use video call software, biometric verification tools, sanctions screening
Ongoing Training (Quarterly):
- Regulatory updates (new FATF recommendations, FinCEN guidance)
- Case studies (recent fraud schemes, sanctions evasion tactics)
- Role-playing exercises (mock KYC calls with actors playing fraudsters)
Quality Assurance:
- Supervisors listen to 10% of calls (random sample)
- Feedback sessions: “Here’s what you did well, here’s what to improve”
- Calibration meetings: All compliance officers discuss edge cases, align on standards

5. User Communication & Transparency
Before Call (24-48 hours notice):
- Email with:
- Clear reason why call needed (“Your account triggered Enhanced Due Diligence due to [transaction volume / jurisdiction / PEP screening]”)
- Checklist of required documents
- Technical requirements (camera, microphone, internet speed)
- Timeline (call will take 15-30 minutes)
- Consequences if call not completed (account restricted after 7 days)
During Call:
- Explain call will be recorded (get explicit consent)
- Set expectations: “This call will take about 20 minutes. I’ll verify your identity, ask about source of funds, and confirm transaction patterns.”
- Professional tone (not interrogational, collaborative: “We’re here to help you complete verification”)
After Call:
- Timeline for decision: “You’ll receive email within 24-48 hours with outcome”
- If additional docs needed: Specific request (“Please provide 2 more months of pay stubs by [date]”)
- If rejected: Vague reason (don’t disclose if SAR filed), explain next steps (withdraw funds, account closure timeline)
Privacy Policy:
- Clear language (not legal jargon): “We store your KYC documents for 5 years per US law”
- Data usage: “Your data used only for verification, not shared with third parties except regulators when legally required”
- User rights: “You can request copy of your data, correct errors, or delete after retention period”
Best Practices for Users: How to Prepare for KYC Calls
1. Document Preparation (48 hours before call)
Government-Issued ID:
- Check expiration date (must be valid for at least 1 month)
- Take high-quality photo in good lighting (if uploading):
- All four corners visible
- No glare or shadows
- Text readable
- Color photo (not black & white)
- Have physical ID ready during call (officer may ask to see original)
Proof of Address:
- Must be dated within 3 months (some exchanges accept 6 months)
- Name must match ID exactly
- Full address visible (street, city, postal code)
- Accepted documents:
- Utility bill (electricity, water, gas, internet)
- Bank statement
- Rental agreement / lease
- Government-issued document with address (tax statement, voter registration)
- NOT accepted (usually):
- Mobile phone bills (some exchanges don’t accept)
- Credit card statements (privacy concerns)
- Hotel receipts, temporary accommodation
Source of Funds (If Requested):
- Employees: Last 2-3 pay stubs + employment contract
- Business owners: Business registration, tax returns (last 2 years)
- Investors: Brokerage statements, property sale documents
- Crypto traders: Transaction history from other exchanges, tax filings showing crypto income
- Be specific: “I earn $X annually from [employer]” not “I have savings”
2. Technical Setup
24 Hours Before Call:
- Test internet speed (minimum 5 Mbps upload – use speedtest.net)
- Test camera: Take selfie, check quality (well-lit, face clearly visible)
- Test microphone: Record voice memo, playback to check clarity
- Download video call platform (Zoom, Skype, custom platform) – test permissions (allow camera/microphone access)
- Choose quiet room:
- No background noise (TV, music, traffic)
- Well-lit (sit facing window or lamp, not backlit)
- Private (no interruptions from family, roommates)
Device:
- Computer preferred (larger screen, more stable than phone)
- If using phone: Stand or prop phone (don’t hold – shaky video)
- Charge device fully (call may take 30 minutes)
3. During Call – Dos and Don’ts
DO:
- Be on time: Join call 2-3 minutes early
- Dress appropriately: Business casual (shows respect, professionalism)
- Have physical ID ready: Officer may ask to see original document
- Answer clearly: Speak at normal pace, don’t rush
- Be honest: If you don’t know answer, say “I don’t know” (don’t guess)
- Ask for clarification: If question unclear, ask officer to rephrase
- Provide specific answers:
- Bad: “I’m a trader”
- Good: “I’m a software engineer at [Company], earning $X annually”
- Stay calm: Nervousness is normal, but don’t be evasive
DON’T:
- Use VPN: Raises red flags (IP location mismatch with stated residence)
- Have others present: Unless pre-approved (spouse for joint account)
- Multitask: Don’t check email, browse web during call (disrespectful, suspicious)
- Give vague answers:
- Bad: “I have business”
- Good: “I own a coffee shop, registered in [City], earning $X annually”
- Rush: Take time to think before answering
- Argue: If officer asks for additional documents, comply (arguing delays process)
4. Security & Privacy Protection
Before Sharing Documents:
- Verify exchange is legitimate:
- Check domain name (phishing sites use similar URLs: coinbaze.com vs coinbase.com)
- Look for HTTPS (padlock icon in browser)
- Cross-reference with official exchange social media, app stores
- Don’t upload KYC to:
- Email attachments (not encrypted)
- Messaging apps (WhatsApp, Telegram – not secure for sensitive docs)
- Third-party websites claiming to “pre-verify” you
- Only upload via official exchange portal (HTTPS, logged-in account)
Protecting Your Data:
- Use unique password for exchange account (not reused from other sites)
- Enable 2FA (authenticator app preferred over SMS)
- Monitor account activity: Check login history, withdrawal addresses
- After account closure: Request data deletion after retention period (5-10 years)
Red Flags (Potential Phishing/Scam):
- Email asking to send ID via reply (exchanges never do this)
- Caller asking for password, 2FA code, seed phrase (NEVER share these)
- Urgent deadline (“Verify in 1 hour or account deleted”) – legitimate exchanges give 7+ days
- Request to install software on your computer during call (potential malware)
5. What If Things Go Wrong?
If Call Drops/Technical Issues:
- Immediately email support: “Call disconnected at [time], can we reschedule?”
- Most exchanges allow 1 free reschedule (no penalty)
If You Don’t Understand Question:
- Say: “Could you rephrase that question?” or “What specifically do you need to know?”
- Don’t guess or make up answer (inconsistency = red flag)
If Officer Seems Suspicious (Potential Scam):
- Verify identity: “Can you provide your employee ID? I’ll call exchange support to confirm.”
- Hang up, call exchange official number (from website, not number provided by caller)
If Verification Fails:
- Ask why: “What documents need improvement?”
- Resubmit clearer documents (better lighting, current proof of address)
- Some exchanges allow appeals (submit written explanation + additional evidence)
If Account Restricted Post-Call:
- Check email for specific reason
- If no clear reason provided: May indicate SAR filed (exchange cannot disclose)
- Withdraw remaining funds if allowed, close account
- Don’t create duplicate account (fraud, permanent ban across industry)
Regional Variations
| Region | Approach | Notable Requirements |
|---|---|---|
| US | Mandatory identity checks | CIP rules, AML compliance |
| EU | Risk-based screening | AMLD5/AMLD6 directives |
| APAC | Pre-service compliance | AUSTRAC, MAS thresholds |
Balancing Privacy & Compliance: Current Reality vs Future Vision
The Fundamental Tension
User Privacy Needs:
- Users don’t want personal data (ID, address, selfie) stored in centralized databases (breach risk)
- Users don’t want to re-upload documents to every exchange (repetitive, time-consuming)
- Users want control over their data (who accesses it, for how long)
Regulatory Compliance Requirements:
- Regulators require exchanges to verify identity, maintain records, file SARs
- FinCEN, MiCA, FCA mandate document retention (5-10 years)
- Independent verification (can’t rely solely on user self-attestation)
The Problem:
- Maximum privacy (user controls all data, nothing stored centrally) conflicts with regulatory requirements (exchanges must store records, verify independently)
- Current KYC = privacy sacrifice for compliance
What Works TODAY (2025): Privacy-Enhancing Measures Within Centralized KYC
1. Encrypted Data Vaults (EDV):
- What: AES-256 encryption for all stored KYC documents
- Access controls: Only authorized compliance officers with MFA can decrypt
- Benefit: Even if database breached, data remains encrypted (useless without keys)
- Limitation: Doesn’t eliminate centralized storage, just protects it
2. Data Minimization:
- Principle: Collect only data required by regulation, nothing extra
- Example:
- Don’t collect: Social security number if not legally required, mother’s maiden name, employment history (unless EDD)
- Collect: Name, DOB, address, government ID (minimum for CDD)
- Benefit: Less data stored = smaller attack surface if breached
3. Purpose Limitation (GDPR Principle):
- Rule: Use KYC data ONLY for verification, not for other purposes
- Example:
- Don’t use: KYC data for targeted advertising (“We see you’re 35, here’s retirement fund ad”)
- Use: KYC data only for AML screening, sanctions checks, age verification
4. User Data Rights (GDPR, CCPA):
- Right to access: User can request copy of their KYC data
- Right to rectification: User can correct errors (wrong address, name spelling)
- Right to erasure: After retention period (5-10 years), user can request deletion
- Right to portability: User can request KYC data in machine-readable format (take to another exchange)
5. Third-Party KYC Providers (Partial Reusability):
- How it works: Verify once with Sumsub/Jumio/Onfido, use across multiple exchanges
- Benefit: User uploads documents once, not to every exchange
- Limitation: Still centralized (KYC provider holds data), privacy risk if provider breached
Experimental Technologies (NOT Compliant for Crypto KYC in 2025):
1. Zero-Knowledge Proofs (ZKP):
- Promise: Prove “I am over 18” without revealing exact birthdate
- Current status: Experimental (Polygon ID, zkMe, Aztec)
- Why not adopted:
- Regulators require full document verification (not just boolean proofs)
- Liability concerns (if ZKP fraudulent, who’s responsible?)
- Technical complexity (users don’t understand how to generate ZKPs)
2. Self-Sovereign Identity (SSI):
- Promise: Users store credentials in own wallet, share selectively
- Current status: Pilot phase (EU eIDAS 2.0, Japan Digital Agency)
- Why not adopted:
- US regulators (FinCEN, SEC, CFTC) have NOT approved SSI for crypto KYC
- <1% exchanges accept SSI credentials
- Regulatory requirement: Exchanges must independently verify, maintain records (SSI alone insufficient)
3. On-Chain KYC Attestations:
- Promise: Cryptographic proof “user verified” on blockchain, without storing documents
- Current status: Very limited (some DeFi projects use, not mainstream CEXs)
- Why not adopted:
- GDPR conflict: Blockchain immutability vs “right to erasure”
- Regulators require document retention (on-chain attestation alone doesn’t satisfy)
- Privacy risk: Public blockchain = anyone can see “User X verified on [date]” (deanonymizes)
Realistic Path Forward (2025-2030):
Short-Term (2025-2027): Incremental Privacy Improvements
- Stronger encryption (post-quantum cryptography)
- Better access controls (zero-trust architecture)
- More frequent audits (quarterly pen tests, annual SOC 2)
- Federated KYC (shared providers like Sumsub – verify once, use multiple exchanges)
Mid-Term (2027-2029): Hybrid Approaches
- SSI pilots gain traction (EU eIDAS 2.0 potentially approved)
- Exchanges may accept SSI credentials + traditional verification (redundant, but satisfies regulators)
- On-chain attestations used for audit trails (blockchain records “verification occurred,” documents stored off-chain)
Long-Term (2030+): Possible Decentralized KYC (Optimistic Scenario)
- Regulators approve ZKP for selective disclosure (prove age without birthdate)
- SSI becomes mainstream (government-issued digital IDs accepted by exchanges)
- Federated identity networks (verify once with government, use across all financial services)
Alternative Scenario: Privacy Remains Limited
- Regulatory inertia (governments don’t approve new technologies quickly)
- Liability concerns persist (who’s responsible if SSI/ZKP fails?)
- Centralized KYC with encryption remains dominant (privacy-enhancing but still centralized)
What Users Can Do NOW to Protect Privacy:
1. Choose Exchanges with Strong Security:
- Look for: SOC 2 Type II, ISO 27001 certified
- Check: Privacy policy transparency (what data stored, how long, who accesses)
- Verify: No history of major breaches OR good response if breach occurred (prompt notification, remediation)
2. Minimize Data Shared:
- Only verify at exchanges you’ll actively use (don’t create accounts “just to check out”)
- If exchange asks for non-required data (e.g., employment history when you’re doing basic trading), question why
3. Use Privacy-Preserving Tools (Where Allowed):
- Monero, Zcash for transactions (privacy coins) – BUT many exchanges delisting due to AML concerns
- Decentralized exchanges (DEXs) for trading without KYC – BUT limited fiat on-ramps, only works for crypto-to-crypto
4. Exercise Data Rights:
- After closing account, request data deletion (after retention period expires)
- Periodically request copy of your data (ensure nothing stored that shouldn’t be)
5. Monitor for Breaches:
- Use haveibeenpwned.com to check if email in known breaches
- If exchange breached, immediately:
- Change password (use unique password, never reused)
- Enable 2FA if not already
- Monitor for phishing (emails claiming to be from exchange)
- Consider freezing credit (if ID documents leaked)
Conclusion: The Reality of KYC Verification Calls in 2025
Key Takeaways:
1. KYC Calls Are Rare, Not Standard
- 95%+ crypto users complete verification through automated eKYC (ID upload + selfie, 5-20 minutes)
- Live verification calls used ONLY for Enhanced Due Diligence (<5% of users):
- Politically Exposed Persons (PEPs)
- Users from high-risk jurisdictions (FATF blacklist countries)
- Large transaction volumes (>$50,000/month varies by exchange)
- Suspicious activity flags (mixing services, sanctioned wallets)
2. Regulatory Compliance Is Non-Negotiable
- US (FinCEN), EU (MiCA), UK (FCA), Asia-Pacific (MAS, FSA, FSC) all mandate KYC for crypto exchanges
- Penalties for non-compliance: Revolut €3.5M (2025), Barclays £42M (2025), FinCEN $210M total fines (2023)
- Record retention required: 5-10 years per AML regulations
3. Centralized KYC Remains the Standard (Despite Privacy Concerns)
- Self-Sovereign Identity (SSI), Zero-Knowledge Proofs (ZKP), on-chain attestations are experimental (pilot phase)
- <1% exchanges accept decentralized credentials in 2025
- US regulators have NOT approved SSI/ZKP as substitute for traditional KYC
- Timeline for mainstream adoption: 2027-2028 earliest (optimistic scenario)
4. Users and Exchanges Both Have Responsibilities
For Users:
- Prepare valid documents (ID, proof of address within 3 months, source of funds if requested)
- Choose exchanges with strong security (SOC 2, ISO 27001, transparent privacy policies)
- Understand when calls are needed (high-risk triggers, not routine verification)
- Protect your data (unique passwords, 2FA, avoid phishing, monitor for breaches)
For Exchanges:
- Implement risk-based KYC (automated for low-risk, calls for high-risk only)
- Secure data storage (AES-256 encryption, access controls, regular audits)
- Train compliance officers (CAMS certified, regular training on fraud detection, cultural sensitivity)
- Transparent communication (clear reasons for calls, timeline, consequences)
The Road Ahead: Realistic Expectations
2025-2027: Incremental Improvements
- Expect: Better biometric accuracy, faster automated verification, shared KYC providers (Sumsub model)
- Don’t expect: Widespread SSI adoption, on-chain KYC replacing centralized databases
2027-2029: Possible Hybrid Models
- Potential: EU approves eIDAS 2.0 (government-issued SSI credentials)
- Exchanges may accept: SSI + traditional verification (redundant, but satisfies regulators)
- US unlikely to approve SSI before 2028 (focus on stablecoin regulation first)
2030+: Decentralized KYC (Optimistic Scenario)
- IF regulatory frameworks established, SSI could supplement (not replace) traditional KYC
- Users with government-issued digital IDs fast-track verification
- BUT: Regulatory inertia, liability concerns may keep centralized KYC dominant
Final Thoughts: Trust Through Transparency
Crypto KYC verification calls, while inconvenient for the small percentage of users who undergo them, serve a critical function: they protect the integrity of the financial system while enabling legitimate users to access crypto services.
The industry is at an inflection point:
- Regulators demand accountability (proven by $210M+ in fines)
- Users demand privacy (breaches at Ledger, Coinbase highlight risks)
- Technology offers potential solutions (SSI, ZKP) but regulatory approval lags
For now, the best path forward is:
- Exchanges: Invest in security (encryption, audits, training), be transparent (clear policies, prompt breach notification)
- Users: Choose reputable exchanges, prepare proper documents, understand your rights (data access, deletion after retention period)
- Regulators: Provide clear guidance on emerging technologies (SSI pilots, ZKP frameworks) to encourage innovation while maintaining compliance
As the crypto industry matures, expect a gradual shift toward privacy-preserving verification methods—but don’t expect overnight transformation. The future of KYC will be built on trust, transparency, and technological progress within the bounds of regulatory compliance.
FAQs
How long does a KYC verification call take?
Typically 10–20 minutes depending on complexity.
What documents are required?
Government-issued photo ID, proof of address, possibly source of funds.
Can I trade without a KYC call?
Some jurisdictions allow limited access, but major exchanges require full KYC.
What happens if I fail the call?
You may be asked to resubmit documents or your account may remain restricted.
Does a KYC call protect me from hackers?
It reduces fraud risk, but securing your own login and wallet is essential.
Is decentralized KYC accepted by regulators?
Acceptance is growing, especially in jurisdictions aligned with GDPR and blockchain innovation.
Read more:
Gaming Outbound Call Strategies to Boost SMB Sales
Video Game Customer Support Strategies for Player Loyalty
Inbound Contact Center Guide Benefits and Best Practices




